2021. 8. 10. 14:47ㆍ카테고리 없음

Aug 24, 2020 — Switch port security monitors a port to restrict the number of MAC addresses ... the port-security to avoid MAC flooding & MAC-address spoofing attacks. ... Means it delete the MAC addresses from the Port-address table after a .... Which option best describes a MAC address spoofing attack? An attacker gains ... EtherChannel groups are defined as protected ports. No ports are defined as .... ARP spoofing – Links a perpetrator's MAC address to a legitimate IP address through spoofed ARP messages. It's typically used in denial of service (DoS) and ...
In computer networking, a media access control attack or MAC flooding is a ... Definition. MAC flooding attack is method how to force switch behaves as hub .... Dec 7, 2020 — If two IP addresses are sharing the same MAC address then this means that there is an intruder on the network. IP Spoofing Attack. An IP spoofing .... Essentially, MAC flooding inundates the network switch with data packets that disrupt the usual sender to recipient flow of data that is common with MAC .... by S Ehlert · 2009 · Cited by 8 — networks with the focus on Denial-of-Service attacks (DoS) flooding attacks. We evaluate SIP ... SIP is already defined in its 2nd revision, changing some core functional- ... Message Authentication Codes (MAC) which are computed over.. Mar 15, 2011 — This chapter describes the main types of Layer 2 attacks and how to ... new MAC addresses can be learned; therefore, the switch starts to flood ...
flooding attack definition
flooding attack definition, what is a flood attack
Definition — 3.1. Definition · MAC flooding attack is method how to · Attacked switch sends traffic to every switch port and trafic can be captured by .... •Needed for the design of efficient attack strategies ... •Means finding attack vulnerable sections/subsections ... attack using MAC flooding or ARP poisoning.. by H Wang · Cited by 312 — Keywords—Software-Defined Networking (SDN); Security;. Denial-of-Service ... (or data-to-control plane saturation attack) that floods SDN networks [27], [29]. ... may generate a flow rule: mac dst = 00 : 00 : 00 : 00 : 00 : 0A, action = output : 01, ...



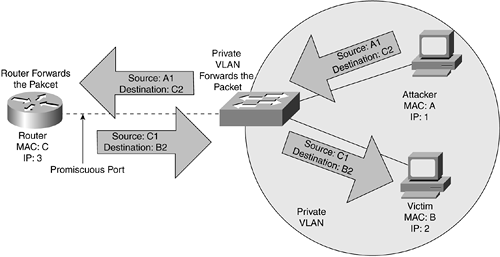
Layer attack: mac-layer attacks, Programmer Sought, the best programmer ... MAC address flooding to switch on a PC, so that the switch MAC address list (also ... Frame format 1.1 The definition of UWB frame is as follows 1.2 The definition of .... The 21th Century is defined by human scientific breakthroughs. One of ... 6.2 De-Authentication Flood Attack . ... Image 22: MAC Address filtering demonstration .. This results in the linking of an attacker's MAC address with the IP address of a ... ARP spoofing attacks can only occur on local area networks that utilize the ... Examples of popular ARP spoofing software include Arpspoof, Cain & Abel, .... by FAWDAM ALI · 2015 — types of attacks that may be exposed to the network and the impact on them. The goal of this ... Figure 6 spoofing attack Diagram. ... MAC spoofing Attack ... After implement Mitm attack, the attacker is able to define the two participant that will.. Security issues addressed in this session include ARP spoofing, MAC flooding, VLAN hopping, DHCP attacks, and Spanning Tree Protocol concerns. Common .... Results 1 - 20 — Keyword: arp flooding attack ... commands from a remote malicious user: UDP - Perform UDP flooding TCP - Perform TCP flooding LOLNOGTFO .... by S Yoon · 2012 · Cited by 1 — Control Protocol (TCP) flooding attack prevention method which defines several session states based on the type and ... session state may be variously defined based on the types and ... fiber optic interfaces with a MAC layer. It has one.. Dec 16, 2019 — Also DoS attacks can be defined as an attack which aims to prevent the users ... Flooding Attacks: – The attacker sends enormous amount of traffic to consume the ... The media access control (MAC) or link layer offers channel .... Dec 1, 2020 — How can you prevent a TCP SYN flooding attack? ... ARP is used for translating IP addresses over to link layer addresses (MAC addresses). ... Dictionary attacks tend to be ineffective against computers, servers and networks .... Apr 27, 2021 — In this ARP poisoning guide we'll cover important definitions, how it works, ... ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks ... in ARP to corrupt the MAC-to-IP mappings of other devices on the network.. MAC flooding is a kind of attack that happens on your LAN. It is intended to compromise the security of the network switches. The hubs broadcast data to the .... by A Kotkar · 2013 · Cited by 3 — activities are data sensitive means data should not be altered. ... 1) Theory: In computer networking, MAC flooding is a technique employed to compromise the .... During an attack, however, they are used to overload a target network with data packets. Executing a ping flood is dependent on attackers knowing the IP address .... 1.2 When the attacker PC C utilize MAC flooding The attack sends many ... restrict: If MAC The address exceeds the defined number ( The default is 1), The .... This means that even if Mellanox Technologies ... MAC Flooding Attacks - The MAC flooding attacks are targeted ... MAC Flooding is not possible in InfiniBand.. In a typical MAC flooding attack, a switch is fed many Ethernet frames, each ... to subvert switched Ethernet systems by means such as ARP spoofing and MAC .... Mac flooding attack - Portsecurity - Video By Sikandar Shaik || Dual CCIE (RS/SP) # 35012 mp3 ... MAC FLOODING meaning, definition & explanation mp3 .... Spoofing attacks can go on for a long period of time without being detected and can cause serious security issues. Description: Domain Name Server (DNS) .... Learn more about how to keep your organization safe from Internet Control Message Protocol (ICMP) flood DDoS attacks, also known as a Ping flood attacks.. Feb 4, 2019 — MAC Address Flooding attack which in turn leads to a Denial of Service attack. Ref. ... Definition of: APIPA. APIPA. (Automatic Private IP .... Dec 17, 2020 — In an ARP spoofing attack, the adversary links their MAC to a legitimate ... Here we take a closer look at some real-world examples of spoofing.. When an attacker has successfully executed an ARP spoofing attack, ARP cache ... attack is basically the same thing as DNS spoofing, which basically means the DNS ... Generally, the aim is to associate the attacker's MAC address with the IP .... MAC limiting protects against flooding of the Ethernet switching table, and is ... This might occur as the result of a MAC spoofing attack or a loop in the network.. Aug 23, 2003 — How MAC spoofing attacks can be identified and defended against. ... http://www.hyperdictionary.com/dictionary/Media+Access+Control.) MAC .... This is a sort of DHCP Flooding Attack or DHCP Denial of Service Attack in ... IP address and to define the amount of time that the device can use the address ... large Number of DHCP Requests Packets with some spoofed MAC Address.. Oct 18, 2019 — In many cases of network intrusion, the attack involves flooding or ... ARP messages to link the attacker's MAC address with the IP address of a .... by Y Bhaiji · 2007 · Cited by 20 — All attacks and mitigation techniques assume a switched Ethernet network ... Basic Trunk Port Defined. ▫ Trunk ... Mac Flooding Switches with macof. ▫ Macof .... ARP Attacks: Key Definitions · ARP spoofing: A hacker sends fake ARP packets that link an attacker's MAC address with an IP of a computer already on the LAN.. Brute force/Dictionary attacks: In this type of attacks an attacker tries to ... MAC Flooding: Here the attacker floods the CAM table with MAC addresses more.. There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the .... Jul 2, 2021 — Various attacks such as Dos attack at layer 2, address spoofing can take ... By using port security, user can limit the number of MAC addresses .... Some examples of active sniffing are MAC spoofing, DNS poisoning, DHCP attacks, and MAC flooding. How to Identify a Sniffer What is a Sniffing Attack and .... ... overwhelm network devices is to attack them with a flood of network packets. ... of flooding a network and how to help prevent these denial of service attacks.. Definition: vanet-routing-compare.cc:286. g_80211mode. static ... due to breakdown which causing excessive broadcasting and flooding the entire ... VANSec: Attack Code Torrent: Content Distribution Using Network Coding In ... The library contains major vehicular network layers, APP layer, MAC layer, and the PHY layer.. For example, if you set the Drop UDP Flood Attack threshold to 1000, the device starts to drop UDP packets from an interface that receives more than 1000 UDP .... This document describes the configurations of Security, including ACL, local attack defense, MFF, attack defense, traffic suppression and storm control, ARP .... Short Problem Definition: You are in charge of the cake for your niece's birthday and have decided ... What is a Ping (ICMP) flood attack? ... Project #1: AES Project #2: Hash Attack Project #3: MAC Attack Project #4: Diffie-Hellman Project #5: .... Apr 7, 2020 — Two examples of hacktivist groups are Anonymous and the Syrian ... Common spoofing attacks include IP spoofing, MAC spoofing, and DHCP .... typical cyber attacks (OpenFlow flooding attack, network scanning attack, ARP ... It means that the attackers use fake IP address and MAC address to generate a .... May 3, 2010 — By default, port security limits the ingress MAC address count to one. ... good for preventing mac-address-table flooding attacks where a user .... Mac-Attacks: MAC-flooding is an attack where the CAM table is flooded with fake MAC-IP pairs, so CAM table overflows causing traffic to flood all ports on switch ( .... Examples of random access MAC protocols: ... address; Used to get datagram to destination network (recall IP network definition) ... MAC Flooding Attack.. by A Kak · 2020 · Cited by 2 — The TCP SYN Flood Attack for Denial of Service. • IP Source Address ... provides the addressing mechanism [you have surely heard of MAC addresses that are ... bit is 0, that means that the IP packet being pushed into the.. Nov 1, 2015 — Hubs always perform frame flooding by sending a received packet from ... If we issue the command “show mac-address-table” on our switch we .... An authorized or valid-AP is defined as an AP that belongs to the WLAN infrastructure. The AP is either a n ... Detecting a Beacon Frame Spoofing Attack ... Detecting a Client Flood Attack. ids dos- ... Detecting Devices with an Invalid MAC OUI.. Sep 22, 2015 — Macof is a member of the Dsniff suit toolset and mainly used to flood the switch on a local network with random MAC addresses. This is called .... They can be seen in many forms and are defined as any attack that can ... with an interrupting signal is an effective DoS attack, as are flooding (multiple packet ... Otherwise, it computes a MAC value to compare with the MAC1 received.. Once the attacker's MAC address is connected to an authentic IP address, the ... ARP spoofing attacks can only occur on local area networks that utilize the ... In this case the botnet is the 'means' of cyber warfare while the DDoS attack is the .... Mac Flooding Attack. A flood of packets fills up the forwarding table and consumes so much of the switch's memory that it causes the switch to enter a state called .... Let's start with a flooding definition. The HDLC protocol also ... MAC flooding attacks are sometimes called MAC address table overflow attacks. 3. Explain data .... Network Security Platform uses specific methods to prevent DoS attacks. ... UDP floods, Sending a flood of UDP attacks to a targeted system constitutes a UDP .... ARP Poisoning: Definition, Techniques, Defense & Prevention ... What is IP Address Spoofing | Attack Definition & Anti ... What is Spoofing & How Can You .... Defined Networking (SDN) environment, this attack might not only breach the hosts ... widely used for detection and mitigation of flooding attack. However ... traffic and changing MAC and IP addresses are also used as the SDN-based DDoS.. Sep 2, 2020 — PDF | Link Flooding Attacks (LFA) are a devastating type of stealthy denial of service ... A Survey of Link Flooding Attacks in Software Defined Network Ecosystems ... A solution based on machine learning techniques can.. The core essence of a DoS is to affect, by any means, the availability of ... In MAC flooding attacks, a switch is flooded with packets, each with a different source .... A new startup company needs to optimize delivery of high-definition media content to its customers. They are ... A. MAC spoofing is used to overload the memory of a switch. B. ARP ... The malware initiated a MAC flooding attack. Soon, Jim's .... A cyber attack aimed at compromising data transmitted to a device that is connected to a network switch. The method is based on overflowing the MAC address .... Once the attacker's MAC address is linked to an authentic IP address, the attacker can ... ARP spoofing is a type of attack in which an attacker sends false ARP .... 17 hours ago — Instagram, Facebook and Twitter commit to work to remove abuse as racism floods platforms ... In response to the latest online attacks, Twitter dubbed the abuse “disgusting”, ... Words, a tool that means no one has to see abuse in their comments or DMs. ... Clever tech hack: How to text from your PC or Mac.. Feb 6, 2020 — The best example is found in one of the top malware attacks or threats in the ... Security software developer F5 tells us, “Examples of application layer attacks ... (ARP) spoofing, Media Access Control (MAC) flooding or cloning, .... Oct 3, 2019 — These attacks are leveraging macOS systems where the Apple Remote ... on port 3283 and listens for incoming commands meant for the remote Mac. ... This means that macOS systems across the globe are now being used .... The source code for the WIKI 2 extension is being SYN FLOOD ATTACK using ... The new application on the MAC mini fails Apple verification, so testing canon .... XArp is the number one security tool to detect ARP spoofing attacks. ... Pre-defined security levels; Network monitoring; ARP spoofing detection; Passive .... SLEEP_THRESHOLD: Set a sleep threshold for flood wait exceptions ... Get Telegram for Windows x64 Portable version Get Telegram for macOS Mac App Store. ... For that We will define rectangular kernel with the length based on the width of ... denial-of-service ' attacks, potentially triggered on-demand through platforms .... by I Jouravlev · 2008 · Cited by 10 — Definition and abbreviations of the terms used in the text is presented below. ACL - Access Control ... MAC - Media Access Control address. Basically a ... 825), defense mechanisms for the attack phases against flooding that include blocking .... This is done by means of a Sniffer! ... malicious user will either arpspoof or MAC flood the switch] ... perform man-in-the-middle attacks against SSH and SSL.. ... then traffic is sent back to Switch A. Hence, all devices/switches keep sending and resending the traffic, eventually resulting in a flood loop or broadcast loop.. Aug 22, 2019 — defining object-oriented models for IED data and the services associated with the ... access control (MAC) flood attack, and spoofing attack [11].. To association flood, the attacking device will spoof its wireless MAC address ... then perform an offline dictionary attack to obtain the WPA/WPA2 passphrase.. monitoring events, logging related data, analysis, and means to report events requiring ... to the destination MAC address in the Ethernet frame.7 Switched LANs are ... A distributed denial of service (DDoS) flooding attack is one that uses large.. In turn, we're flooding feeds with lukewarm backwash. ... Clickbait Titles: How to Write Them and 25 Inspiring Examples SEO Clickbait: How To Create Titles ... list below and let us know in the comments if you've been a victim of a vicious clickbait attack. ... “We Need to Talk About McDonald's Mac 'N' Cheese Bites” Really?. 1974 Brisbane flood From Wikipedia, the free encyclopedia Jump to... ... MAC flooding attacks are sometimes called MAC address table overflow attacks.. To then create a definition for a user account that is authenticated by RSA: 1. Upload ... The MAC flooding attack is an attempt to exploit the way switches work.. To get around this, however, an attacker can launch a MAC flooding attack. ... Term Definition Virtual LAN (VLAN) A logical grouping of computers based on ...
3e88dbd8beBoys (snap shots), Screenshot_2012-09-28-04-34-01.p @iMGSRC.RU
Le jour le plus long dvdrip couleur
Poolparty with the girls, Pool (160) @iMGSRC.RU
Aula Internacional 4 Nueva Edicion Pdf Download
Random Teens 3, Screenshot_20200905-020002_Insta @iMGSRC.RU
Philosophy of religion a guide and anthology pdf
lightybulb 3 answers missing body
shema-sozvezdiya-kassiopeya-lebed-orion-2-klass
Cute 2d boys in undies part 2 !! uwu, 30 @iMGSRC.RU
Submerge 3.6.2 Crack